In the world of ops, it’s natural not to want to patch/update a finicky application. What sys admin wants to break sh*t?! Interestingly, Equifax’s former CEO blamed the entire data breach on the sys admin that didn’t patch Apache Struts.
Fortunately, working in the Department of Defense, we have systems in place that alert us to running out-of-date vulnerable software and make patching it a priority.
Working as a sys admin on a network that is part of the Department of Defense (DoD), you pretty much know that any non-current software is game to be flagged when the security alerts are released each week. You can count on your quarterly Java, Apache, OpenSSL updates to be required. Windows updates are never-ending.
DoD policy requires routine network device/server/workstation scans that look for security findings. On the network on which I work, we scan at least weekly The scanner uses a plugin database that receives nightly updates from DISA. The majority of plugins typically correspond to Information assurance vulnerability alerts (IAVA) that are derived from CVEs.
These plugins do more than just checking for out-of-date vulnerable software. They also will also check for security configuration issues like weak SSL ciphers or expired SSL certificates.
Below, you’ll see a sample detailed vulnerability finding.
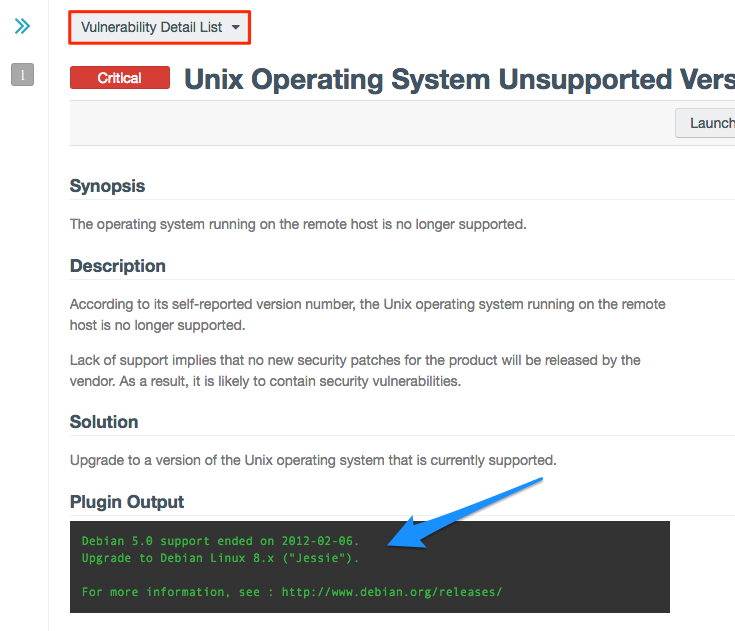
SOURCE: https://www.tenable.com/sites/drupal.dmz.tenablesecurity.com/files/images/blog/SC3a.png
Once a vulnerability has been detected, in most cases, we have two weeks to patch/remediate the issue. For my command, if we can’t meet the deadline, we need to work with our Cyber Security Team to write a POAM that lists how this finding is reduced risk and when it will be fixed. These plans ultimately will need to be approved by a much higher echelon.